Configuring SAML for Encodify through Google
Overview
Setting up SAML SSO for Encodify using Google as an Identity Provider (IdP) involves configuring both Google and Encodify IDP to communicate securely and authenticate users using SAML messages.
Configuration includes 2 main steps:
Configuration of Custom SAML App in Google Workspace
Configuration of the Identity provider in Encodify
Configure Custom SAML App in Google Workspace
Note!
Configuration of the SAML App in Google workspace requires access to the Admin Console.
Sign-in to Google Admin Console.
Go to Menu > Apps > Web and mobile apps.
Click Add App > Add custom SAML app.
Enter a name for the SAML app and click Continue.
Click Continue on the next step where Google SAML attributes are displayed.
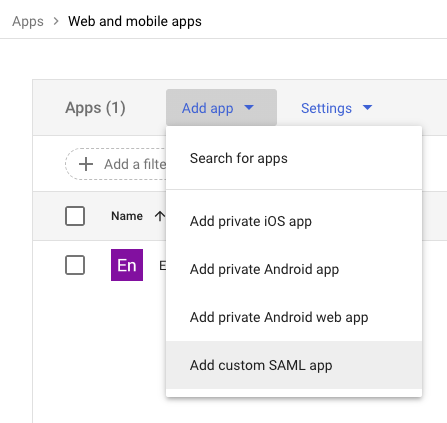
Enter the following settings on the next step. Both values can also be found by downloading the Encodify SAML metadata document that is available under the following URL in Encodify: https://worker/context:443/saml/metadata. Note, that this URL can also be found on Step 3 of the SAML IDP configuration wizard page in Encodify.
ACS URL: https://worker:443/context/saml/SSO
Entity ID: https://worker:443/context/saml/metadata
Leave the default values for the Name ID format and Name ID fields > Click Continue.
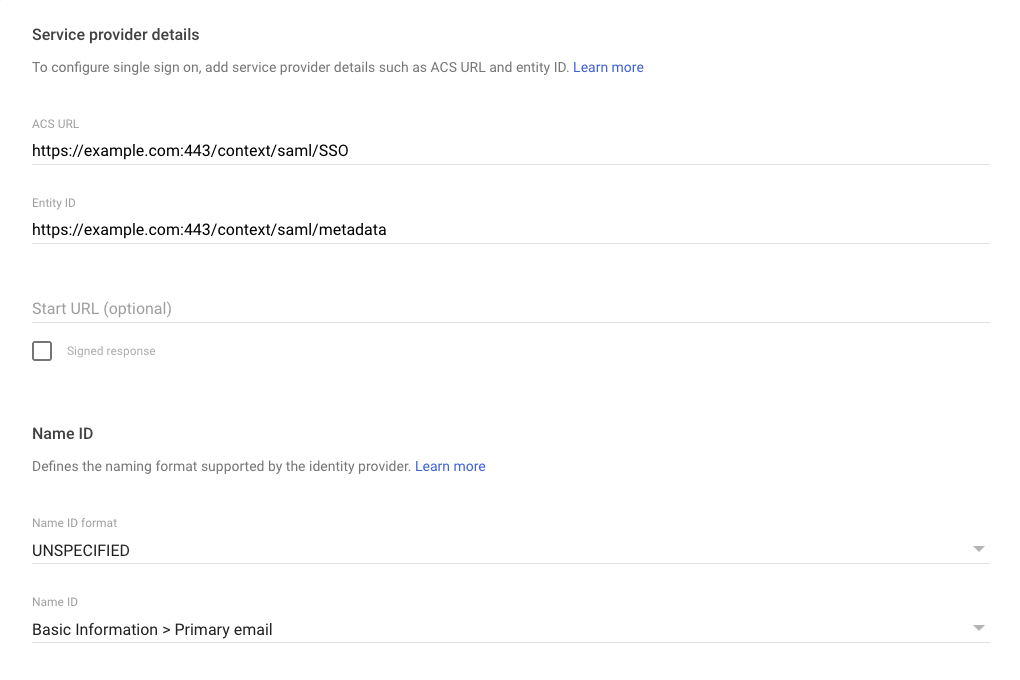
On the last configuration step it is possible to add mappings of the Google directory and App attributes. Attributes mapped here will be present in SAML metadata that will be used for authentication under SSO. Note, that it is required to map user email attribute which is the primary and unique user identifier in Encodify.

Click Finish. After saving, new app will appear in the list of Webapp and mobile Apps.
Configure Identity Provider in Encodify
After SAML app has been created and configured in Google, corresponding SAML IDP needs to be created and configured in Encodify.
Follow the configuration wizard setps to configure the Identity Provider.
Steps 1-2:
Go to Site Configuration > Identity Providers and User > Identity Providers and follow the configuration steps described here until Step 3: Details
Step 3:
There is no public link to Metadata xml file provided by Google, therefore it will be needed to download the metadata XML file and make it publicly available.
File can be downloaded from Google Admin console > Apps > Web and mobile apps > click your previously created app > click “Download metadata”.
After making file publicly available, enter the link URL in the Federation Metadata field.
In the External User ID Attribute field, enter the app attribute representing user’s email (app attribute configured in Attributes mapping in Google).
In the Attributes mapping section, map additional Google attributes to the User fields in Encodify, if needed.
Click Next when done.

Step 4
In case access rights for the auto-provisioned users need to be set based on user attributes in Google, follow this guide for instructions.
Step 5
In case user groups for the auto-provisioned users need to be set based on user attributes in Google, follow this guide for instructions.
Step 6 - 7
Follow this guide in case default Encodify user properties need to be configured for the auto-provisioned users.
Step 8
Follow this guide if you need to configure welcome email and login message.
After IDP is saved, the corresponding SSO login button will be displayed on the log in page. This will allow users to get authenticated using their google workspace login credentials.