Overview
Encodify supports Single Sign-On (SSO) through integration with external Identity Providers (IdPs), allowing users to authenticate securely using their corporate credentials. This streamlines access management and enhances security across the platform.
Encodify supports authentication using the following methods:
Internal (Basic Authentication)
OpenID Connect (OIDC)
OAuth 2.0
SAML 2.0 (Scheduled for deprecation)
Why use an Identity Provider
Integrating your IdP with Encodify enables:
Centralised user authentication - Manage user credentials and access from a single source.
Improved security controls - Leverage your IdP’s advanced security features, such as MFA and access policies.
Simplified user lifecycle management - Streamline provisioning, deprovisioning, and role updates as users join, leave, or move within the organisation.
Enhanced user experience - Provide a frictionless login experience with one-click access via SSO.
Authentication Methods
Internal (Basic Authentication)
Users are created manually within Encodify and authenticate using a username and password. Passwords can be reset by users directly through the application. Best suited for standalone use cases or testing environments.
OpenID Connect (OIDC) – Recommended
An identity layer on top of OAuth 2.0, OIDC allows users to log in with a single set of credentials via trusted providers (e.g., Microsoft, Google). It is the preferred protocol for modern SSO implementations in Encodify.
Supported OIDC Providers:
Google Identity / Google Workspace
Okta
Microsoft Entra ID (formerly Azure AD)
Microsoft Active Directory Federation Services (AD FS)
Amazon Cognito
OAuth 2.0
OAuth 2.0 enables secure, delegated access to Encodify resources without requiring the sharing of credentials. This is ideal for systems requiring token-based, delegated authentication from a third-party identity provider. The diagram below provides an overview of OAuth 2.0:
SAML 2.0
Important: Support for SAML 2.0 is currently under review. If you are using SAML 2.0 today, we recommend planning your transition to OpenID Connect, which provides better compatibility with modern authentication standards and infrastructure.
SAML is an XML-based protocol that uses security assertions for user authentication and authorisation. While still supported for now, it is scheduled for deprecation in favour of OIDC. The diagram below illustrates SAML authorisation:
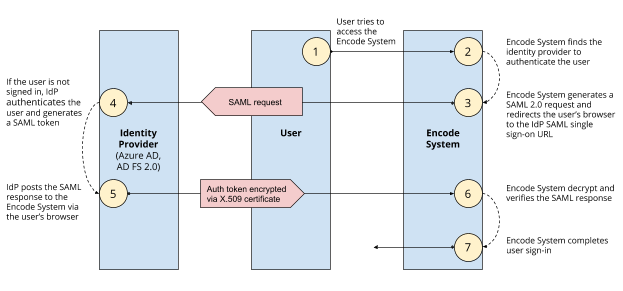
Supported SAML Providers:
Google Identity / Google Workspace
Okta
Microsoft Entra ID (formerly Azure AD)
Microsoft Active Directory Federation Services (AD FS)
Amazon Cognito
Considerations
If your Encodify system doesn't have an IdP set up, users can log in using their username and password through the login form.
Once you add at least one IdP (OpenID, SAML or OAuth2) that matches a specific login URL, the login form will no longer be available on that Login Page. Visiting that Login URL will take you straight to the external provider's login page. If you don't have a profile there, you won't be able to access Encodify anymore.
We recommend always having an alternative Login URL without an IdP assigned (or just using an Internal IdP) so you can still access Encodify and make changes if something goes wrong.
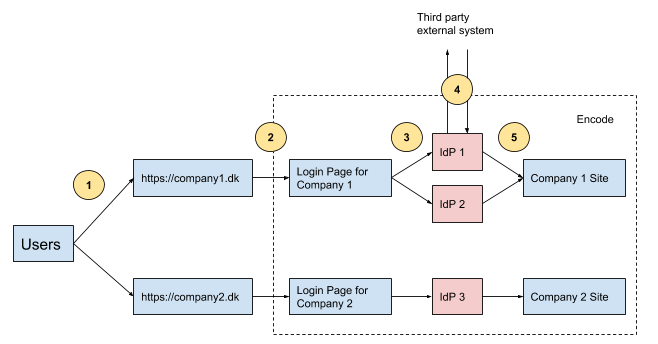
Login Page
Login Page with SSO
Each Identity Provider (IdP) integration in Encodify is linked to a corresponding login page that defines how users access the platform. The diagram below illustrates three common authentication methods:
Manual login using a username and password (internal authentication)
Single Sign-On (SSO) via Microsoft Entra ID (formerly Azure AD)
SSO via Google Workspace