Overview
This article provides step-by-step guidance on how to configure Microsoft Entra ID (formerly Azure Active Directory) for Encodify using OpenID Connect (OIDC).
Configuring OpenID Connect for Encodify via Microsoft Entra ID
Step 1: Start IdP Configuration in Encodify
Navigate to: Site Configuration → Identity Providers and Users → Identity Providers.
Click Add New IdP.
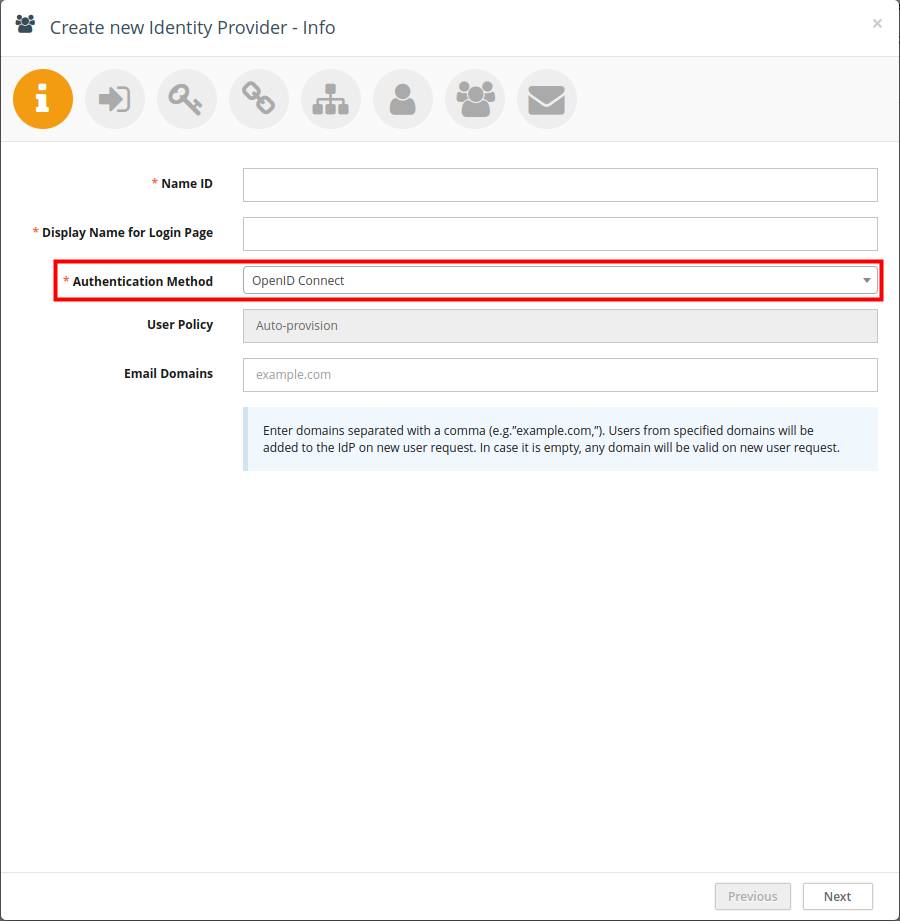
Fill in the fields as follows:
Name ID: Use only English letters without spaces. This will be part of the URL.
Display Name for Login Page: This will be shown on the login button.
Authentication Method: Select OpenID Connect.
Email Domains (optional): Specify allowed domains (e.g.
encode.dk, microsoft.com).
Click Next to proceed to Step 2.
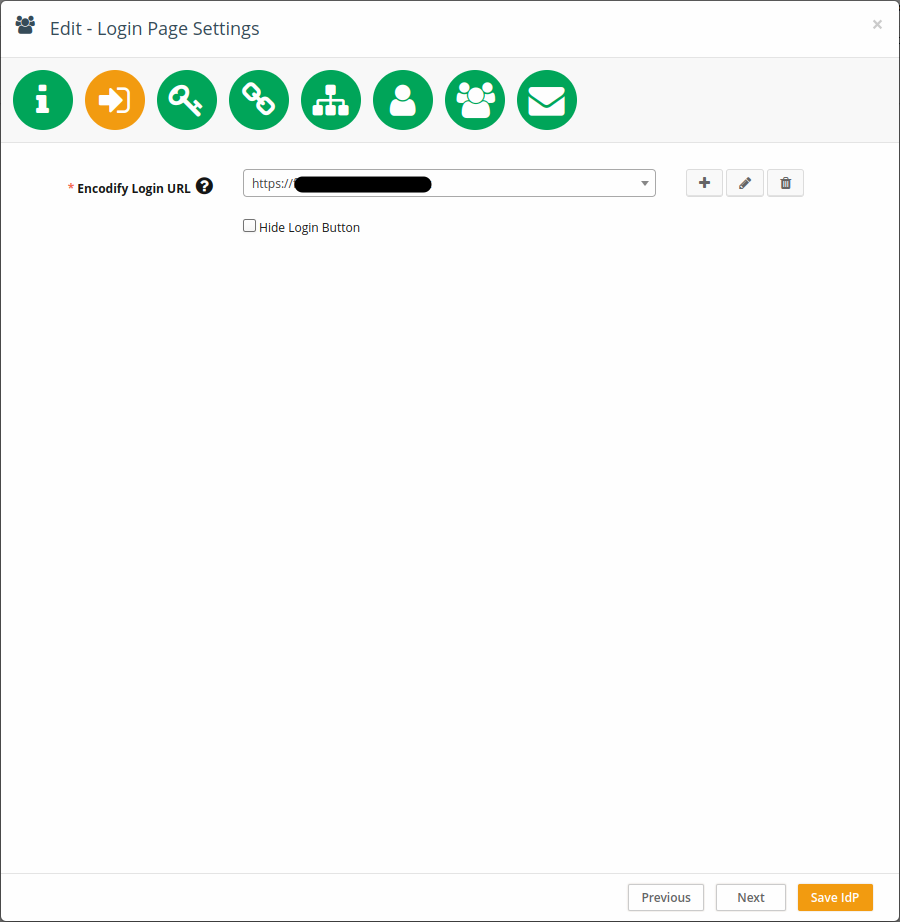
Step 2: Link to a Login URL
Link your IdP configuration to an existing Login URL and Login Page, or create new ones.
Each IdP can be linked to only one Login URL.
Click Next to proceed to Step 3.
Step 3: Copy Callback URL
Copy the Callback URL provided on this page. You'll use it when setting up your Entra ID app.
Step 4: Create OAuth Credentials in Microsoft Entra Admin Center
Register a New Application
Go to the Microsoft Entra Admin Center and log in.
Use the search bar to navigate to App registrations.
Click + New registration.
Enter the Name for your application.
Click Register.
Configure Authentication
In your new application's left menu, click Authentication.
Click + Add a platform and choose Web.
Paste the Callback URL copied from Encodify.
Click Configure.
Generate Client Secret
Navigate to Certificates & Secrets.
Click + New client secret.
Add a Description and choose an Expiration period.
Click Add and copy the Client Secret (you'll use this in Encodify).
Get OpenID Configuration URL
Go to the Overview page of your Entra ID app.
Locate and copy the Directory (tenant) ID and Application (client) ID.
Find the OpenID Connect metadata document link—this is your OpenID Configuration URL.
Format:
https://login.microsoftonline.com/<tenant-id>/v2.0/.well-known/openid-configuration
Step 5: Complete IdP Configuration in Encodify
In Step 3 of the Encodify IdP setup, enter your OpenID Connect Config URL (from Step 7).
Encodify will auto-fetch the following:
OpenID Connect JWK URI
OAuth2 Authorization URL
OAuth2 Access Token URL
Fill in the remaining fields manually:
Field | Value |
|---|---|
OAuth2 Client ID | From Entra App Registration |
OAuth2 Client Secret | From Entra Client Secret |
OAuth2 Scope |
|
External User ID Attribute |
|
Click Next to proceed to further steps (e.g., access rights, default groups, etc.) as needed.
Note: Microsoft Entra ID does not support mapping of custom user claims beyond standard ones (e.g. name, email).
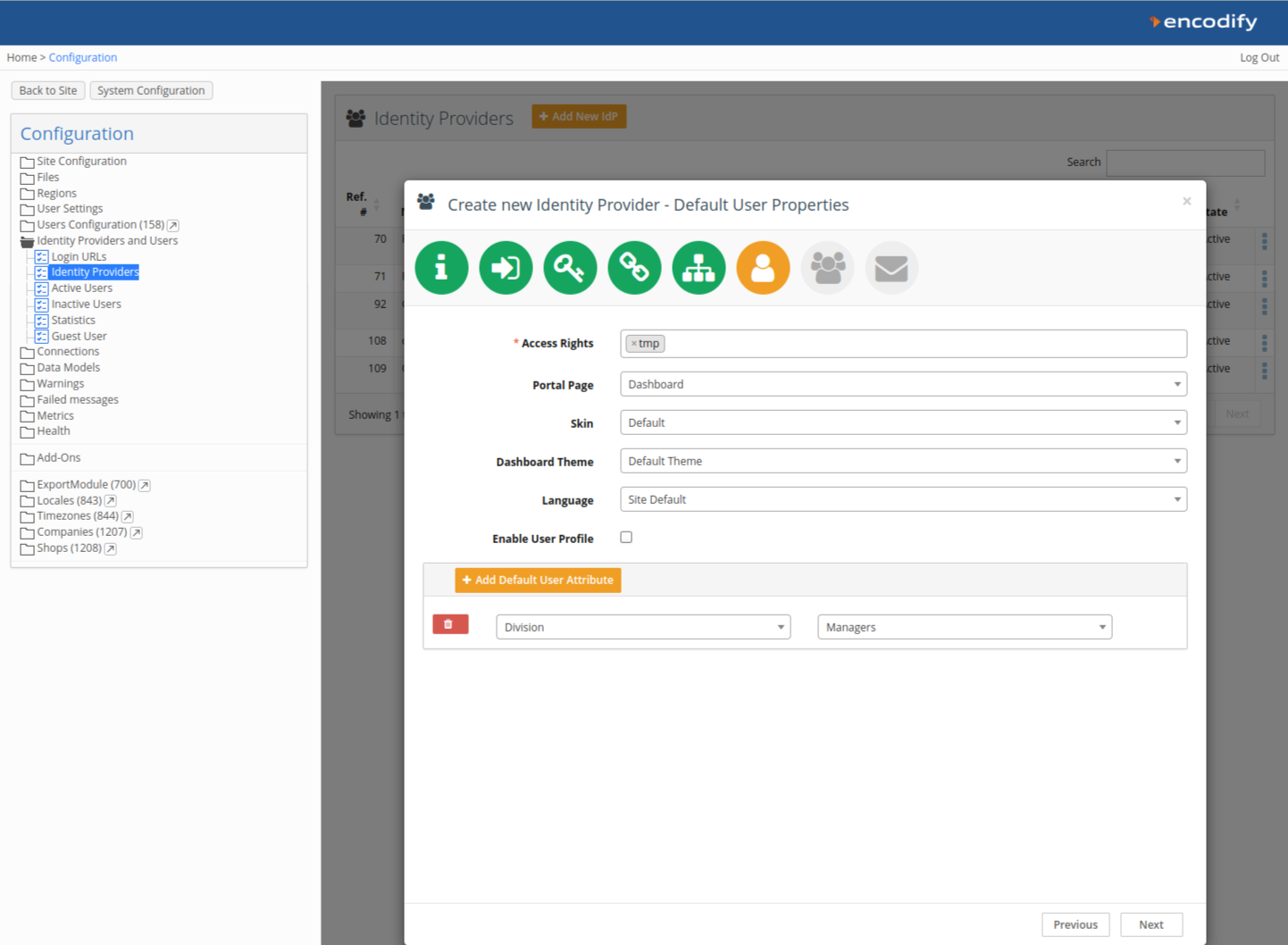
Step 6: Default User Groups
Define default groups to assign on first login.
Click Next.
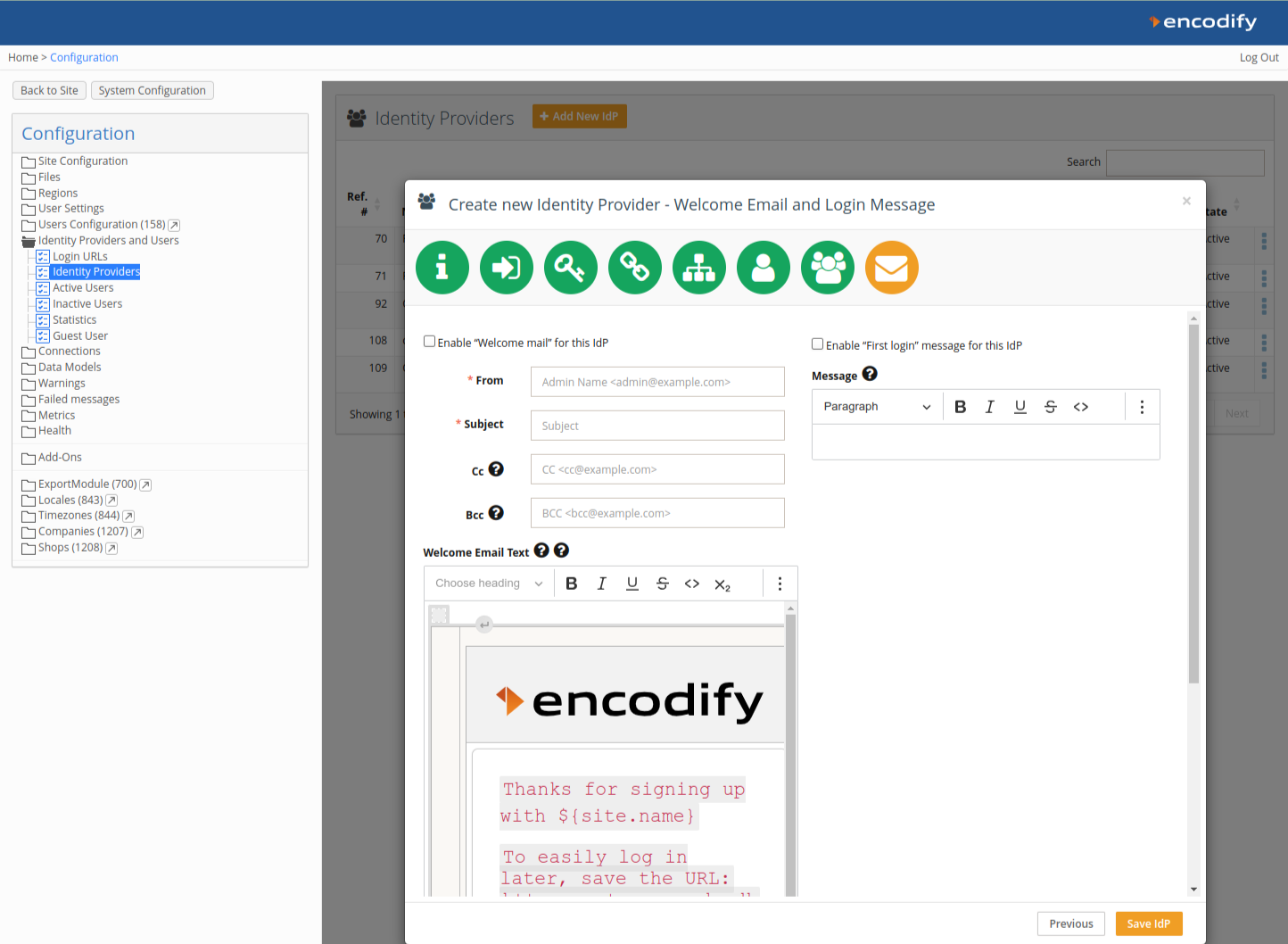
Step 7: Welcome Message & First Login Email
Optionally enable a Welcome Email and First Login Message.
Click Save IdP to complete the setup.
Logging In via Microsoft Entra ID OIDC
If Entra ID is the only method linked to the Login URL, users are redirected directly. If multiple methods exist, users will see a button (e.g. Sign in with Microsoft). Upon first login, users will be auto-provisioned in Encodify with configured roles and attributes.