Configuring SAML for Encodify through Azure
Receiving the Federation Metadata URL
Sign in to your Azure portal page using the following URL: https://portal.azure.com/ (Microsoft account should be created in order to be able to sign in).
Go to Active Directory service (if you don’t have it on the sidebar, click More services and find it the service list). Note, that Active Directory service is available only for an account with a paid subscription (you can use free trial subscription for testing purposes).
Assuming you already have a specific directory created (otherwise you can use default directory or create a new one using New icon).
Click App registrations menu in the Manage section on the left sidebar.
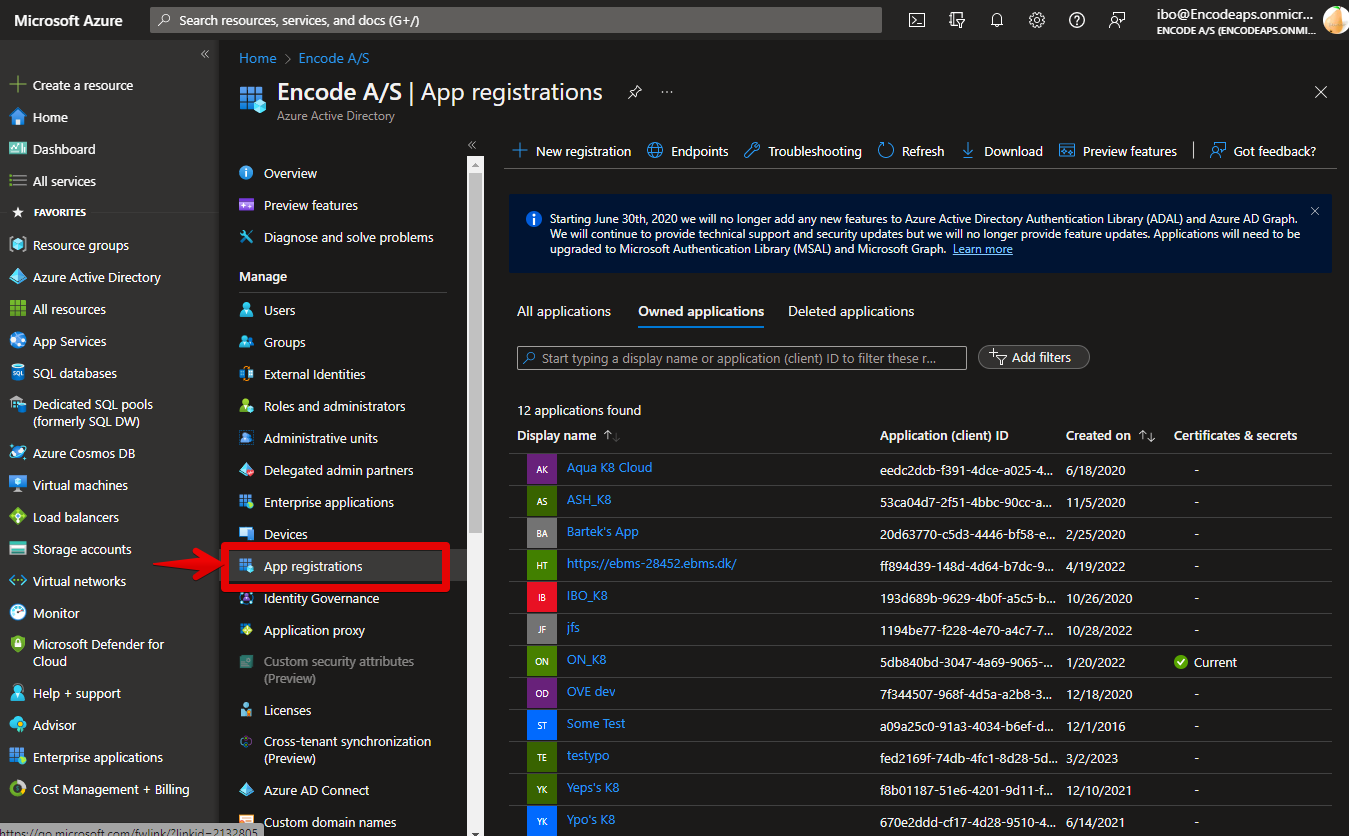
Go to application list window and click Endpoints button. Find Federation Metadata Document endpoint URL. You need it when configuring Azure AD IdP profile in Encodify system.
Configuration of SAML Application
Click New registration in the application list window that is appeared (it might be initially empty).
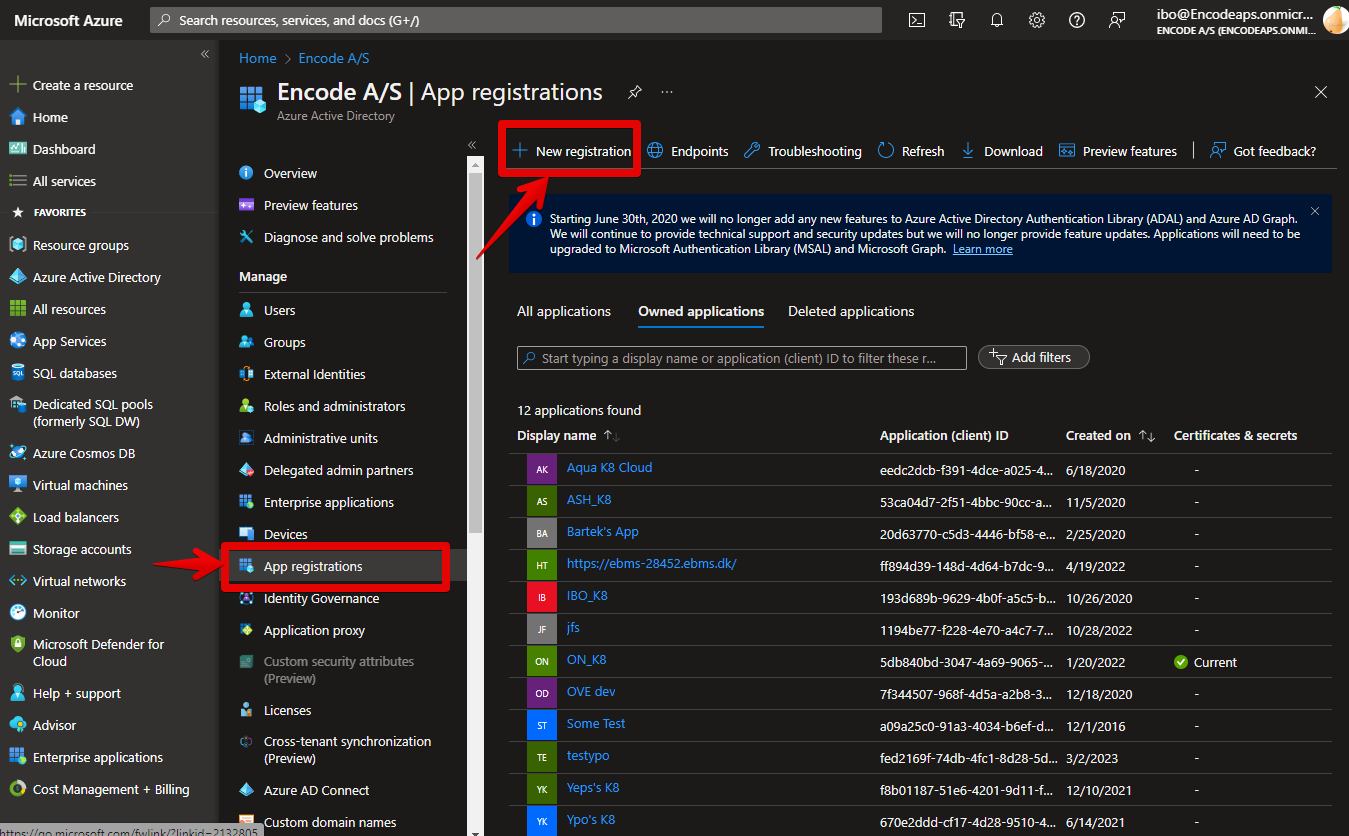
Specify initial settings for the new app in the Register an Application window appeared and confirm settings clicking the Create button on the bottom:
Parameter
Description
Example
Name
Application name, minimum 4 characters length
SAML Connect
Supported account type
Who can use this application
Encodify only - Single tenant
Redirect URI
URI to which Microsoft Azure AD will send SAML authentication tokens for authenticated users.
{encodeServerURL}:{port}/{worker}/saml/SSOWeb
https://qa.test.com:443/qa/saml/SSO
Beware of new requirements from Microsoft/Azure that custom domains have to be verified. If we are hosting the system on Encodify domain (*.encodify.com) we need to add a TXT/MX record to our DNS settings. If it is hosted on a client domain (encode.client.com) then it must be done by the client.
See more: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/add-custom-domain
Switch to the Manifest tab in your app window.
In the Edit manifest window, which shows the settings in JSON format, specify the next parameters (you can find these in your IdP settings In Encodify system):
Parameter
Description
Example
groupMembershipClaims
Enables sending user groups in SAML token
All
identifierUris
The URI used as a unique logical identifier for your Encodify system:
{encodeServerURL}:{port}/{worker}/saml/metadatahttps://qa.test.com:443/qa/saml/metadata
replyUrlsWithType
URI to which Microsoft Azure AD will send SAML authentication tokens for authenticated users.
{encodeServerURL}:{port}/{worker}/saml/SSOhttps://qa.test.com:443/qa/saml/SSO
{ "id": "15db0d06-4b48-44be-a2ac-ca51c92c0c9d", "acceptMappedClaims": null, "accessTokenAcceptedVersion": null, "addIns": [], "allowPublicClient": false, "appId": "dbc79949-9d63-4778-827f-26eb1fd7b3f2", "appRoles": [ { "allowedMemberTypes": [ "User" ], "description": "Read-only access to device information", "displayName": "Read Only", "id": "601790de-b632-4f57-9523-ee7cb6ceba95", "isEnabled": true, "lang": null, "origin": "Application", "value": "ReadOnly" } ], "oauth2AllowUrlPathMatching": false, "createdDateTime": "2018-09-04T12:20:22Z", "description": null, "certification": null, "disabledByMicrosoftStatus": null, "groupMembershipClaims": "All", <----- 1 "identifierUris": [ "https://qa.test.com:443/qa/saml/metadata" <----- 2 ], "informationalUrls": { "termsOfService": null, "support": null, "privacy": null, "marketing": null }, "keyCredentials": [], "knownClientApplications": [], "logoUrl": null, "logoutUrl": null, "name": "SAML Connect", "notes": null, "oauth2AllowIdTokenImplicitFlow": true, "oauth2AllowImplicitFlow": false, "oauth2Permissions": [ { "adminConsentDescription": "Allow the application to access YPO on behalf of the signed-in user.", "adminConsentDisplayName": "Access YPO", "id": "f2a01a5f-4880-4249-9b89-9a2b6f3757c5", "isEnabled": true, "lang": null, "origin": "Application", "type": "User", "userConsentDescription": "Allow the application to access YPO on your behalf.", "userConsentDisplayName": "Access YPO", "value": "user_impersonation" } ], "oauth2RequirePostResponse": false, "optionalClaims": null, "orgRestrictions": [], "parentalControlSettings": { "countriesBlockedForMinors": [], "legalAgeGroupRule": "Allow" }, "passwordCredentials": [], "preAuthorizedApplications": [], "publisherDomain": null, "replyUrlsWithType": [ { "url": "https://qa.test.com:443/qa/saml/SSO", <------- 3 "type": "Web" } ], "requiredResourceAccess": [ { "resourceAppId": "00000002-0000-0000-c000-000000000000", "resourceAccess": [ { "id": "311a71cc-e848-46a1-bdf8-97ff7156d8e6", "type": "Scope" }, { "id": "a42657d6-7f20-40e3-b6f0-cee03008a62a", "type": "Scope" } ] } ], "samlMetadataUrl": null, "signInUrl": "https://qa.test.com:443/qa/", "signInAudience": "AzureADMyOrg", "tags": [], "tokenEncryptionKeyId": null }Save Manifest settings using Save button.