Overview
To protect against password-guessing attacks, the system supports two types of login blocking mechanisms: Soft Blocking and Hard Blocking.
Soft Blocking temporarily disables the login page after a set number of failed login attempts. Users are prevented from logging in during this time but may still use the “Forgot your password” feature. After the defined blocking period, access is automatically restored.
Hard Blocking deactivates a user account after repeated failed attempts. Once inactive, the user cannot log in or reset their password. Reactivation requires administrative action.
Where to find Block User Login
To locate the Block User Login settings, navigate to System Configuration → Users → Block User Login. This section allows you to configure both soft and hard blocking options to enhance account security.
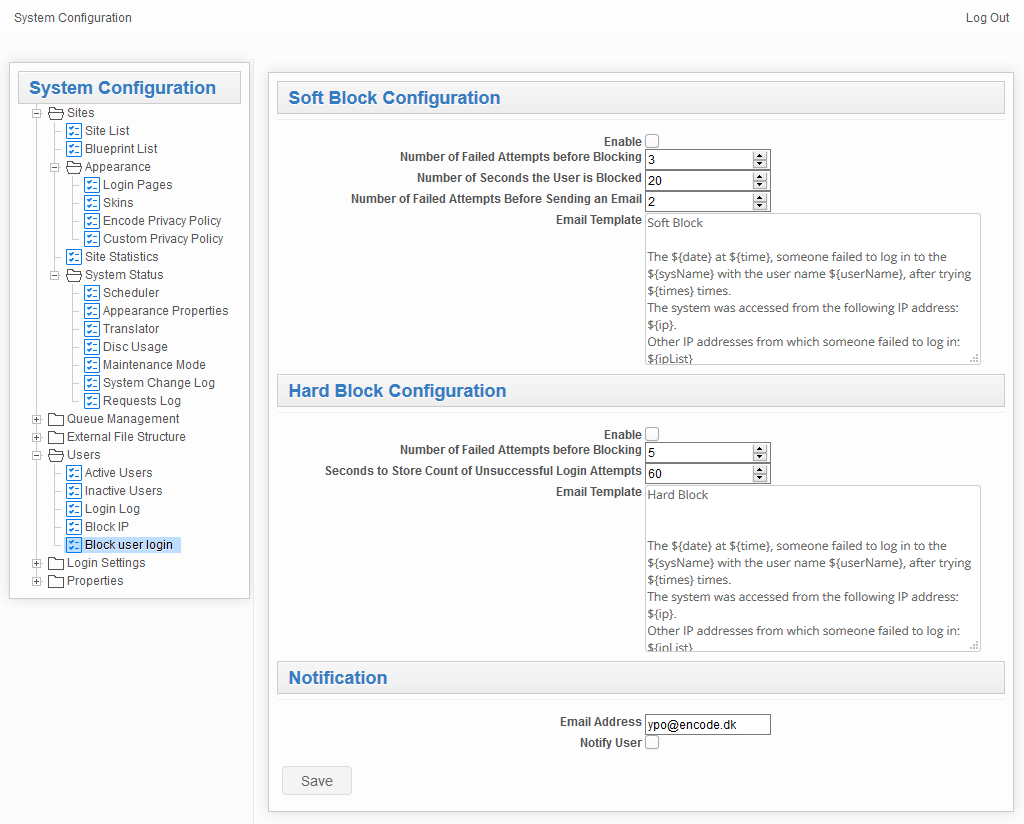
Soft Block Configuration
To activate soft blocking functionality, configure the following parameters:
Parameter name | Description |
|---|---|
Enable | This parameter enables soft blocking, which prevents further login attempts by temporarily blocking access to the login page. It is disabled by default. |
Number of Failed Attempts before Blocking | Specifies the number of failed login attempts after which the login page will be blocked to prevent further attempts. The default value is 3. |
The duration in seconds that the login page will be blocked after the user reaches the number of failed login attempts specified in the Number of Failed Attempts Before Blocking property. The default duration is 20 seconds. | |
Number of Failed Attempts Before Sending an Email | The number of failed login attempts that trigger sending an email notification about a possible attack. |
Template for the emails sent to notify the addresses specified in the Email Address property about a possible attack. | |
Blocking mail properties | Includes placeholders that will be replaced with actual data:
|
Note!
The number of already performed failed login attempts will be reset in the following cases:
After login page blocking time elapses
After the user logs in successfully
The user resets his password via the Forgot your password functionality
The application server is restarted
Hard Block Configuration
To activate the hard blocking functionality, configure the following properties:
Parameter name | Description |
|---|---|
Enable | This parameter enables a hard block that deactivates a user after a specified number of failed login attempts. It is disabled by default. |
Number of Failed Attempts before Blocking | The number of failed login attempts after which the user will be deactivated. Once inactive, the user will be unable to log in, even with correct credentials, and cannot reset their password via the “Forgot Your Password” feature. The default value is 10. |
Seconds to Store Count of Unsuccessful Login Attempts | The period during which failed login attempts are recorded. After this period expires, the count of failed attempts resets to zero. The default duration is 24 hours, starting from the first failed login attempt. |
Email Template | A template for the emails sent to notify the specified addresses (in the Email Address property) about a potential attack. |
Notification
Configure alerts sent to admins or users when thresholds are reached:
Parameter name | Description |
|---|---|
Email Address | The email address(es) to which notifications about a potential attack will be sent after the user exceeds the number of failed login attempts specified in the Number of Failed Attempts Before Sending an Email property. Multiple addresses can be specified, separated by commas. |
Notify User | Enables sending a notification email to the user whose account is under attack. Emails are sent according to the threshold set in the Number of Failed Attempts Before Sending an Email property. Disabled by default. |